It usually starts the same way.
An alert comes in overnight. Maybe it is an email from a security vendor. Maybe it lands in a shared inbox. Maybe it shows up in a dashboard no one looks at until Monday morning. Someone flags it for review. Someone else plans to “circle back.” The business keeps running.
By the time anyone actually opens the alert, the damage is already done.
I have seen this pattern repeat itself across industries, company sizes, and technology stacks. Smart organizations. Capable IT teams. Well-funded security tools. All undermined by a single assumption that feels reasonable on the surface but is deeply flawed.
“We’ll review the alert when we have time.”
As a CISO, I can tell you with absolute certainty that time is the one thing attackers are counting on you not having.
The Illusion of Safety in Traditional SOC Models
Most organizations today are not ignoring security. They have invested in endpoint protection, firewalls, email security, identity controls, and vulnerability scanners. Many even outsource monitoring to a third-party security operations center.
On paper, this looks mature.
In practice, it often plays out very differently.
The traditional SOC model is built around alerting, not action. A tool detects something suspicious. A ticket is generated. An email is sent. The customer is notified and expected to review and decide what to do next.
This workflow assumes a few things that are no longer true.
- It assumes threats move slowly.
- It assumes humans can review alerts faster than attackers can move.
- It assumes that tomorrow is soon enough.
None of those assumptions hold up anymore.
Attackers Do Not Work on Your Schedule
One of the most dangerous myths in cybersecurity is that risk accumulates gradually. That breaches happen after weeks or months of neglect.
The reality is far more unforgiving.
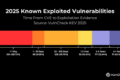
According to VulnCheck’s Known Exploited Vulnerabilities data for 2025, exploitation happens fast. Nearly 29 percent of known exploited vulnerabilities are leveraged within the first 24 hours of public disclosure. That is not days. That is not weeks. That is before most organizations even finish their morning coffee.
Another 9 percent are exploited within the first month. Over a quarter are exploited within the first year. And importantly, exploitation does not stop after the headlines fade. Vulnerabilities continue to be abused years later, long after patching urgency has evaporated.
The takeaway is simple and uncomfortable.
You do not get to choose when attackers act. They choose for you.
Why “We’ll Patch It Soon” Is Not a Strategy
I spend a lot of time talking to business leaders who feel caught in the middle. They understand the risk. They also understand the reality of operations.
You cannot patch every firewall, server, endpoint, and application every single day. You cannot reboot production systems on demand. You cannot pause the business every time a new vulnerability is disclosed.
Attackers know this too.
That gap between disclosure and remediation is where real-time detection and response becomes critical. If you cannot eliminate exposure instantly, you must be able to detect abuse instantly and respond without delay.
Waiting for an alert to be reviewed days later is not risk management. It is wishful thinking.
The Real Problem Is Not Tooling. It Is Latency.
When breaches happen, organizations often blame missing tools. In most cases, the tools were already there. The alert fired. The log was generated. The signal existed.
What failed was time.
Time between detection and response.
Time between alert and action.
Time lost to inboxes, ticket queues, and handoffs.
In security, latency is risk.
An hour can be the difference between a blocked login attempt and a compromised administrator account. A day can be the difference between isolated malware and full lateral movement. A weekend can be the difference between contained exposure and ransomware.
This is why Forthright does not measure success by alerts delivered. We measure it by actions taken.
What Real-Time Detection Actually Means
Real-time detection is not about staring at dashboards 24 hours a day. It is about building systems and processes that assume threats will move quickly and are designed to move faster.
At Forthright Cyber, our SOC operates 24×7 with an anomaly-detection framework that looks for behavior that does not fit normal patterns. Not just known signatures. Not just yesterday’s threats. But deviations that suggest something is wrong right now.
When those signals appear, they are reviewed by trained analysts who are empowered to act. Not to notify. Not to suggest. To respond.
For critical issues, our escalation paths reach senior security staff immediately. We target a 15-minute response window because anything longer is often too long.
That response may involve containment, isolation, credential resets, or automated actions through Security Orchestration Automated Response playbooks. These playbooks are documented, tested, and audited. They are not improvised in the middle of an incident.
This matters more than most organizations realize.
Automation Without Oversight Is Just Another Risk
Automation is powerful. Used incorrectly, it is dangerous.
One of the reasons many internal IT teams hesitate to automate responses is fear. Fear of disrupting the business. Fear of shutting down the wrong system. Fear of breaking something that matters.
Those fears are valid when automation is not governed.
At Forthright Cyber, our SOAR actions are designed around real-world attack paths like business email compromise. They are built with safeguards. They are reviewed regularly. They are executed by analysts who understand both the technology and the business impact.
Automation accelerates response, but humans remain accountable.
This balance is what allows us to act in minutes instead of days.
Why Overextended IT Teams Cannot Win This Fight Alone
Internal IT teams are under enormous pressure. They manage infrastructure, support users, deploy projects, and keep the business running. Adding 24×7 security monitoring and response on top of that is unrealistic.
Even the best teams cannot respond to an alert at 2:00 a.m. with the same speed and clarity as a dedicated SOC that does nothing else.
This is not a criticism. It is a structural reality.
When alerts pile up overnight or over a long weekend, response time stretches. Attackers do not wait for Monday.
The Hidden Cost of Delayed Decisions
Every delayed response carries a cost that rarely shows up in a budget line item.
- Business disruption.
- Customer trust erosion.
- Regulatory exposure.
- Executive time consumed by crisis management.
I have never sat across from a CEO after an incident who said, “I’m glad we waited to respond.”
The question is never whether an alert was received. It is whether anyone acted in time.
What Business Leaders Should Be Asking Instead
If you are a business owner or executive, the most important security question is not “What tools do we have?”
It is “How fast do we respond when something goes wrong?”
Ask your providers how long it takes from detection to action. Ask who makes the decision to contain a threat. Ask what happens at 3:00 a.m. on a holiday weekend.
If the answer involves emails, tickets, or next-day reviews, you already know the risk.
Cybersecurity is no longer about building higher walls. It is about shortening response time.
Attackers move in minutes. Vulnerabilities are exploited in hours. Waiting days is no longer defensible.
At Forthright Cyber, we built our SOC, our platform, and our processes around one principle: when something matters, speed matters more.
If you are ready to move beyond alerts and into real-time protection, we should talk. Your business deserves more than a notification after the fact. Give us a call or send us an email now. We’re here for you.

With a commitment to revolutionizing how businesses operate, Forthright empowers organizations to unlock the full potential of secure and compliant digital workspaces, enabling employee productivity.